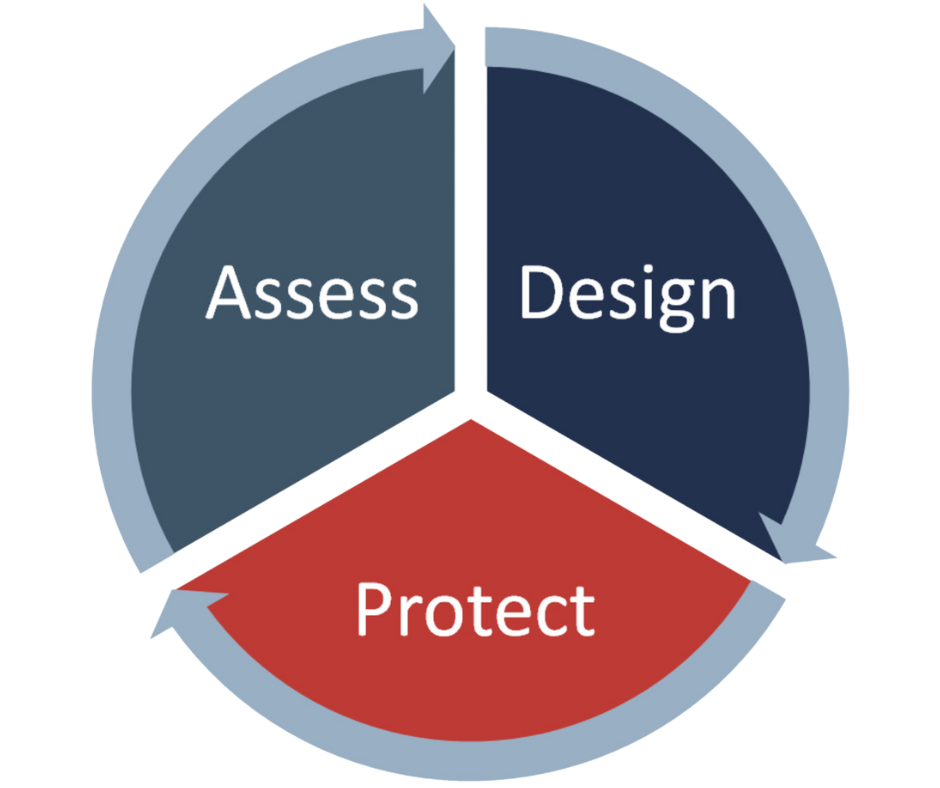
ASSESS
Gain clarity on your current security and compliance controls, paired with a roadmap for future improvements.
Avertium assesses your security environment to get a comprehensive view of your technology investment, compliance landscape, attack surface, and risk posture.


























.png?width=500&height=200&name=qcm%20technologies%20logo%20(1).png)







